It has come to my attention that there are a few default
settings for
Outlook , Outlook Express, and Windows itself that should be changed
before we receive even one more email with attachments written
in the HTML language which is capable of automatically launching
attached scripts and executables.
1. Left click on the ![]() button in the Windows task bar.
button in the Windows task bar.
2. From the {Programs} menu select ![]()
3. Left click to open the {View} menu, then left click on the last
selection
in that menu {Folder Options...}
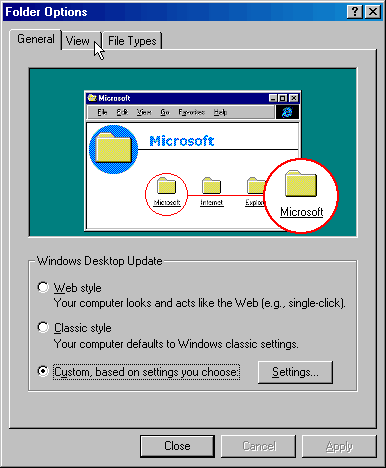

4. Left click on the {View} tab as shown above.
5. Left click to place a bullet next to:
{Show all files}
and to remove the check from beside
{Hide file extensions for known file types}
as illustrated above.
6. Left click on the [Apply] button.
7. Close Windows explorer.
Now we will be able to see the full
file name for email
attachments. This is important because in the case of
the "ILOVEYOU.TXT.vbs" if one were to receive this
email without having disabled
{Hide file extensions for known file types}
the attachment would appear only as "ILOVEYOU.TXT"
which might lead one to not worry about its contents since there
is no known way to transmit a virus via a (.txt) file.
The (.vbs) file extension is what
should have caught everyone's eye.
This extension stands for Visual Basic Scripting.
Which is a simple programming language that interacts
with the Windows Scripting Host. The Scripting host translates
commands from Visual Basic into the Windows system commands
which are what drove the payload of this virus. One should not
expect to receive a letter of any sort from someone that employed
the (.vbs) technology in its creation.
Apart from the file extension
differences you may also
tell (.vbs) files from others by the icon that windows
assigns these files.

If you receive any file with the .vbs extension you should take every
precaution before attempting to open this file. I personally would never
open any (.vbs) file even if it was from someone I knew unless
You knew for certain that the person who sent it created it themselves
and that they did so without implementing any harmful code
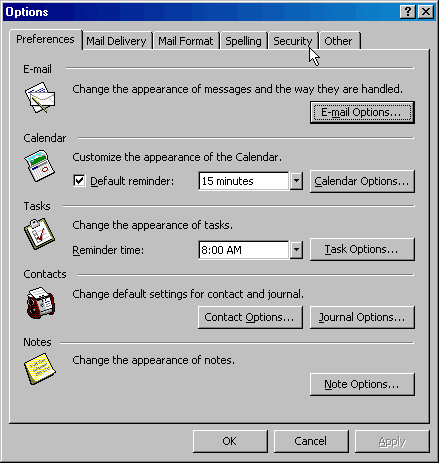
11. Open Outlook 2000
12. Left click on the {Tools} menu and
then select
the {Options} selection from the bottom of that menu.
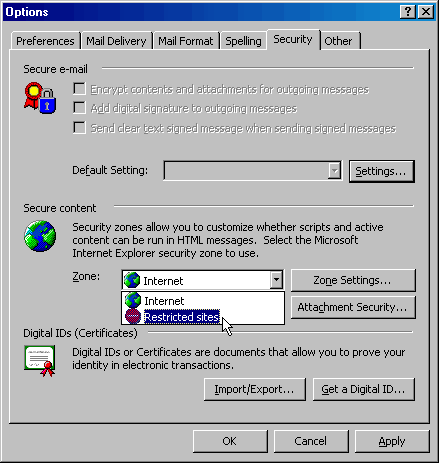
13. Left click on the Security tab as shown above to the left.
14. In the Secure content portion use the pull
down menu
to select the Restricted sites option.
15. Left click on the [Attachment Security...] button.
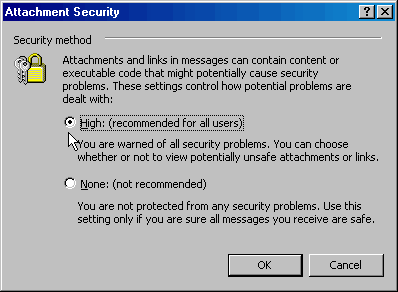
By default this setting is already on {High:} when you
install Outlook
However I suggest making sure it has not been changed somehow
before assuming it is indeed that way.
16. Left click on the [OK] button in the Attachment Security
prompt.
17. Left click on the [Apply] button in
the Security/Options
prompt and then left click on the [OK] button.
You have now made it safe to use the preview pane in Outlook
2000 again.
When you do receive an unsafe message you will see the .vbs icon
in the preview header beside the regular paper clip.

Any attempt to execute this script in the preview pane will result in the following prompt:
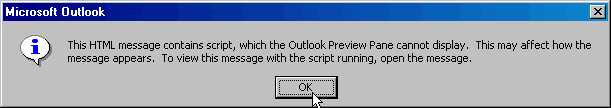
At this point you should attempt to get what you can from the
preview pane and promptly delete
the message without ever fully opening it neither should you attempt to open its
attachment as
the script was most likely designed to do that very thing and would have,
without intervention
from you, had you not followed the steps in this walkthrough.
P.S. This walkthrough is basically the same for outlook
express except the windows for step 13 and 14
look like this:
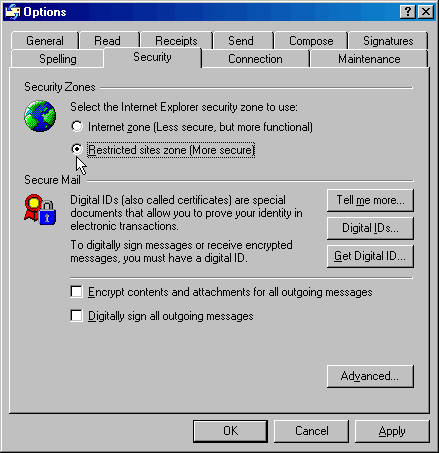
and step 15 is omitted for this program.